Contents
| Inhalt | ||||||
|---|---|---|---|---|---|---|
|
...
The configuration file htpasswd.d/osgi-htpaswd.htpasswd specifies one or more osgi-runner users in the domain osgi, like this snippet from the default configuration shows:
| Codeblock | ||||
|---|---|---|---|---|
| ||||
osgi:$apr1$a2pxQc6X$fc.1CQ0UO.rkhXwKXdWeZ. karaf:$apr1$eQJ1yFFI$q/orCEOYMpcoplIBAxpcg/ |
...
We very strongly recommend to change the password to something worthy of being called a password, or restrict administrative access vectors by other means (Firewall, ReverseProxy font, ...).
In typical environment the authentication will be changed from JAAS to an auth backend like LDAP/ADS.
Optional: Configuring the embedded SSH Server
...
The port and address to listen on can be configured in the configuration file etc/conf.d/gogo-ssh.properties. The major lines of the default configuration are:
| Codeblock | ||||
|---|---|---|---|---|
| ||||
# location of the authorized_keys file
gogo.ssh.etcPath = ${osgi.runner.etcPath}/sshd.d
# port and address to listen on
gogo.ssh.port = 8101
gogo.ssh.host = localhost |
...
Felix' HTTP port is configured in the configuration file file adm.d/org.apache.felix.http.cfg which looks like this:
...
osgi-runner should only listen on localhost (127.0.0.1), which is achieved by adding the setting org.apache.felix.http.host=127.0.0.1 to org.apache.felix.http.cfg, see also http://felix.apache.org/documentation/subprojects/apache-felix-http-service.html for more configuration options of the embedded HTTP server.
Alternatively, the local firewall should not allow remote access to osgi-runner's HTTP port.
...
Create and configure the configuration PID org.clazzes.login.ldap, for details see https://confluence.clazzes.org/display/LOGIN/org.clazzes.login.ldap
Key | Value | Remarks |
|---|---|---|
defaultDomain | DOMAIN | Replace DOMAIN by your Windows domain name. |
domain.DOMAIN.controllerUri | ads://domain.top | Lookup of LDAP server in DNS via _ldap._tcp SRV entries, adapt to your DNS domain name, replace DOMAIN in key name by your Windows domain name. |
domain.DOMAIN.authMethod | bindAds | Bind to LDAP using ADS conventions, replace DOMAIN in key name by your Windows domain name. |
After having set up the ADS connection you should be able to sign on the the given ADS domain using the login form given at http://localhost:8081/http-login/org.clazzes.login.ldap/login
...
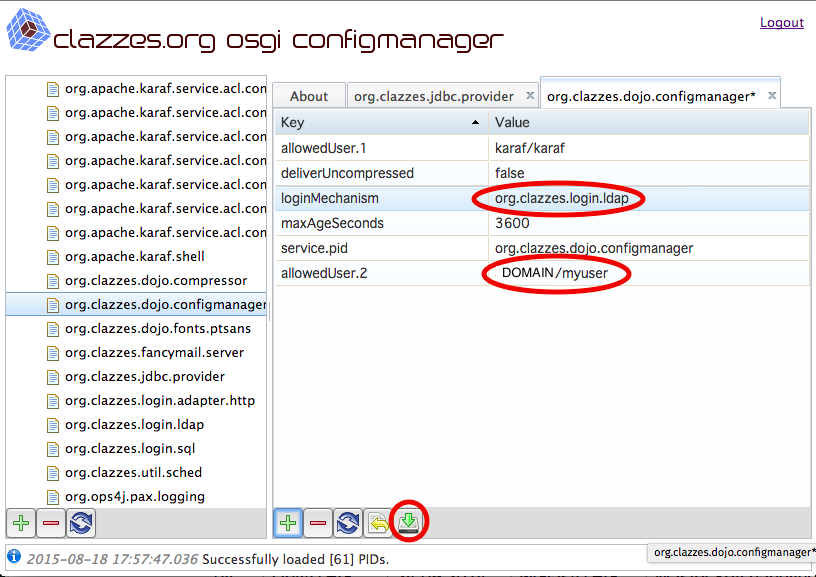
Configure the configuration PID org.clazzes.dojo.configmanager and change the following settings:
Key | Value | Remarks |
|---|---|---|
| loginMechanism | org.clazzes.login.ldap | Change to the above configured login adapter |
| allowedUser.2 | DOMAIN/<myuser> | <myuser> is the Windows logon name of an allowed user. Once LDAP access is working, you may also overwrite the allowedUser.1 entry. Replace DOMAIN by your Windows domain name. |
| allowedUser.3, AllowedUser.4,... | DOMAIN/<yetanotheruser> | You may add additional entries allowedUser.3, AllowedUser.4,... |